How to Configure SSH on Cisco Router or Switch?
Enable SSH on Cisco Router and Configure SSH on Cisco Router or Switch.
Short and complete guide to configure SSH on Cisco router and switch for secure remote connection. The Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. The best-known example application is for remote login to computer systems by users.
SSH provides a secure channel over an unsecured network in a client-server architecture, connecting an SSH client application with an SSH server. Common applications include remote command-line login and remote command execution, but any network service can be secured with SSH. The protocol specification distinguishes between two major versions, referred to as SSH-1 and SSH-2.
The typical use of SSH Protocol
The protocol is used in corporate networks for:
- providing secure access for users and automated processes
- interactive and automated file transfers
- issuing remote commands
- managing network infrastructure and other mission-critical system components.
Configure SSH on Cisco Router or Switch
To configure SSH on Cisco router, you need to do:
- Enable SSH on Cisco router.
- Set Password for SSH.
- Force remote access to use SSH.
- Enable Password Encryption.
- Add domain name Server (DNS).
- Add Username and Password.
Let’s enable and configure SSH on Cisco router or switch using the below packet tracer lab. The configure on a packet tracer lab and real Cisco devices are the same. Just try to learn and do it what the SSH remote authentication needs.
Download the packet tracer lab or create your own lab. SSH Configuration Packet Tracer Lab.
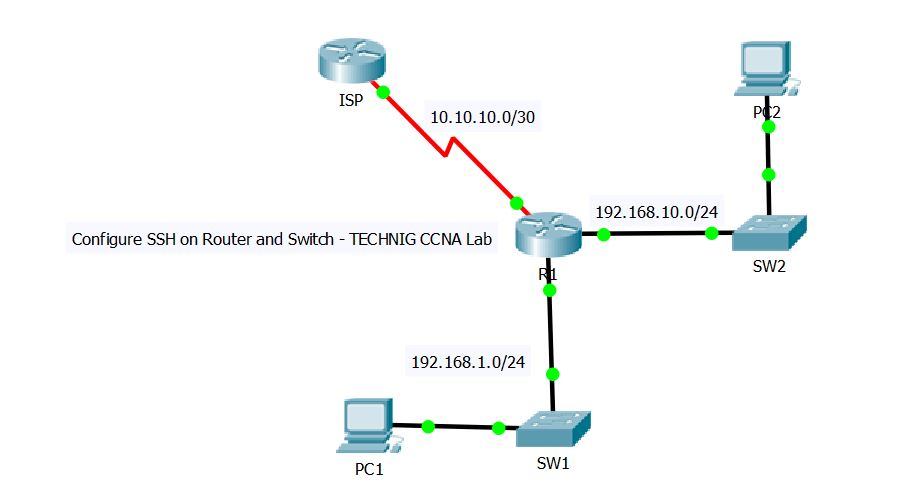
In this example, I just enable and configure SSH on SW1 and trying to access it from PC1. It’s enough to learn how to configure SSH on Cisco router.
R1> R1>enable R1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. R1(config)# R1(config)#ip domain-name Technig.com R1(config)#crypto key generate rsa The name for the keys will be: R1.Technig.com Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes. How many bits in the modulus [512]: 1024 % Generating 1024 bit RSA keys, keys will be non-exportable...[OK] R1(config)# *Mar 1 0:5:57.974: %SSH-5-ENABLED: SSH 1.99 has been enabled R1(config)# R1(config)#username Admin password Technig R1(config)#line vty 0 4 R1(config-line)#login local R1(config-line)#transport input ssh R1(config-line)#exit R1(config)#ip ssh version 2 R1(config)#ip ssh authentication-retries 3 R1(config)# R1(config)#ip ssh time-out 120 R1(config)#exit R1#
That’s all. Let’s check the process one by one.
- I have set DNS domain name with “IP domain-name” command.
- Then configure the router to use RSA key pair with modulus size of 1024 bites for remote service authentication with “crypto key generate rsa” command.
- Add username “Admin” with Password of “Technig” for ssh authentication.
- Enabled ssh with “line vty 0 4” command.
- Configure ssh to use local username and password with “login local” command. Remember that you can set a username and password for ssh with “username Admin password Technig” command as well. But here we configure ssh to use local username and password.
- Configure the router to accept only ssh connection with “transport input ssh” command.
- Configure ssh to version 2 using “IP ssh version 2” and set the authentication times to 3 with “IP ssh authentication-retries 3” command.
- Finally set the ssh timeout to 120 seconds with “IP ssh time-out 120” command.
Related Article: Install SSH on CentOS 8.x and Red Hat Linux
The final step is to test the connectivity of ssh from PC1 with “ssh -l Admin 192.168.1.1” command for command prompt.
C:\>ssh -l Admin 192.168.1.1 Open Password: R1>en R1>enable Password: R1#
OK, the ssh works perfectly.
