Do you know what are the best ways to mitigate VLAN attacks in the network switching? Here we just explain VLAN threats and mitigate VLAN attacks. The VLAN architecture simplifies network maintenance and improves performance, but it also opens the door to abuse. A specific type of VLAN threat is a VLAN hopping attack. The Switch spoofing is a type of VLAN hopping attack, A switch interface which is connected to an end device (a computer or a printer) are normally in access mode and that end device will have access to its own VLAN.
How to Mitigate VLAN Attacks?
The VLAN hopping is a computer security exploits, a method of attacking networked resources on a virtual LAN (VLAN). The basic concept behind all VLAN hopping attacks is for an attacking host on a VLAN to gain access to traffic on other VLANs that would normally not be accessible.
The best way to prevent basic VLAN hopping attacks:
- Disable DTP (auto trunking) negotiations on non-trunking ports by using the switchport mode access interface configuration command.
S5(config)# interface range fa0/1 - 14 S5(config-if-range)# switchport mode access S5(config-if-range)# exit
- Manually enable the trunk link on a trunking port using the switchport mode trunk interface configuration command.
S5(config)# interface range fa0/15 - 18 S5(config-if-range)# switchport mode access S5(config-if-range)# switchport access vlan 899 S5(config-if-range)# shutdown S5(config-if-range)# exit
- Disable DTP (auto trunking) negotiations on trunking ports using the switchport non-negotiate interface configuration command.
- Set the native VLAN to be something other than VLAN 1 and to be set on an unused VLAN using the switchport trunk native vlan vlan_number interface configuration mode command.
S5(config)# interface range fa0/19 - 24 S5(config-if-range)# switchport mode trunk S5(config-if-range)# switchport nonegotiate S5(config-if-range)# switchport trunk native vlan 900 S5(config-if-range)# exit
- Disable unused ports and put them in an unused VLAN.
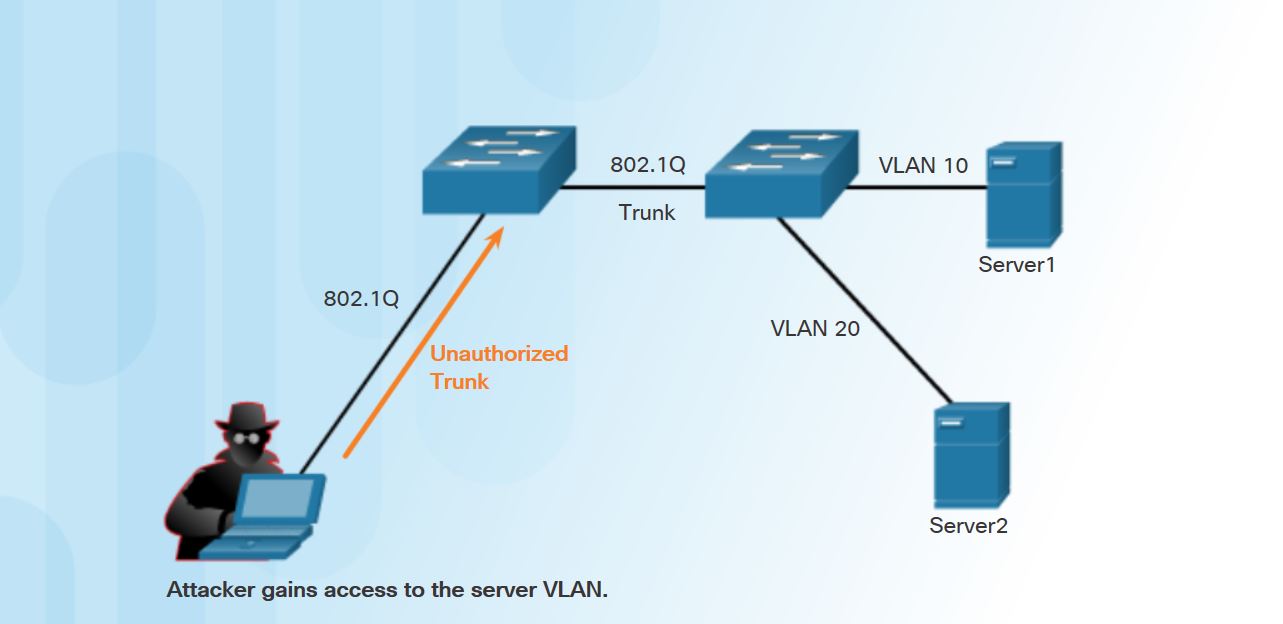
A VLAN hopping attack can be launched in one of two ways:
- Spoofing DTP messages from the attacking host to cause the switch to enter trunking mode. From here, the attacker can send traffic tagged with the target VLAN, and the switch then delivers the packets to the destination.
- Introducing a rogue switch and enabling trunking. The attacker can then access all the VLANs on the victim switch from the rogue switch.
Double-Tagging Attack
Another type of VLAN hopping attack is a double-tagging (or double-encapsulated) attack. This attack takes advantage of the way hardware on most switches operates.
- Step 1. The attacker sends a double-tagged 802.1Q frame to the switch. The outer header has the VLAN tag of the attacker, which is the same as the native VLAN of the trunk port. The assumption is that the switch processes the frame received from the attacker as if it were on a trunk port or a port with a voice VLAN. (A switch should not receive a tagged Ethernet frame on an access port.) For the purposes of this example, assume that the native VLAN is VLAN 10. The inner tag is the victim VLAN; in this case, it is VLAN 20.
- Step 2. The frame arrives on the switch, which looks at the first 4-byte 802.1Q tag. The switch sees that the frame is destined for VLAN 10, which is the native VLAN. The switch forwards the packet out on all VLAN 10 ports after stripping the VLAN 10 tag. On the trunk port, the VLAN 10 tag is stripped, and the packet is not retagged because it is part of the native VLAN. At this point, the VLAN 20 tag is still intact and has not been inspected by the first switch.
- Step 3. The second switch looks only at the inner 802.1Q tag that the attacker sent and sees that the frame is destined for VLAN 20, the target VLAN. The second switch sends the frame on to the victim port or floods it, depending on whether there is an existing MAC address table entry for the victim host.
This type of attack is unidirectional and works only when the attacker is connected to a port residing in the same VLAN as the native VLAN of the trunk port. Thwarting this type of attack is not as easy as stopping basic VLAN hopping attacks.
The best approach to mitigating double-tagging attacks is to ensure that the native VLAN of the trunk ports is different from the VLAN of any user ports. In fact, it is considered a security best practice to use a fixed VLAN that is distinct from all user VLANs in the switched network as the native VLAN for all 802.1Q trunks.
PVLAN Edge Configuration
Some applications require that no traffic be forwarded at Layer 2 between ports on the same switch so that one neighbour does not see the traffic generated by another neighbour.
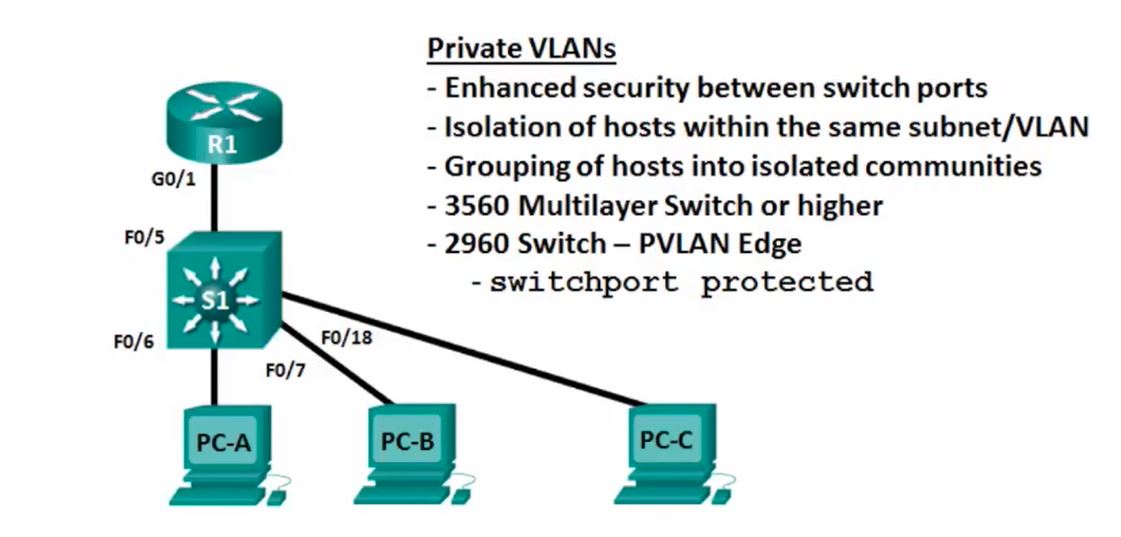
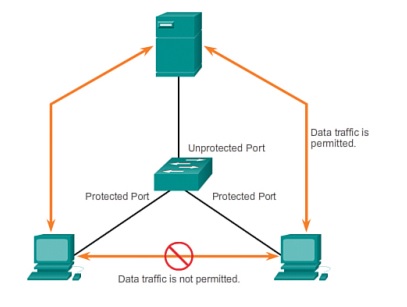
In such an environment, the use of the PVLAN (Private VLAN) Edge feature ensures that there is no exchange of unicast, broadcast, or multicast traffic between PVLAN edge ports on the switch, as shown in the figure. The PLVAN Edge feature is also called Protected Ports.
The PVLAN Edge feature has the following characteristics:
- A protected port does not forward any traffic, such as unicast, multicast, or broadcast, to any other port that is also a protected port. Data traffic cannot be forwarded between protected ports at Layer 2; only control traffic is forwarded because these packets are processed by the CPU and forwarded in software. All data traffic passing between protected ports must be forwarded through a Layer 3 device.
- Forwarding behaviour between a protected port and a non-protected port proceeds as usual.
- The default is to have no protected ports defined.
To configure the PVLAN Edge feature, enter the switchport protected interface configuration mode command.
S5(config)# interface g0/1 S5(config-if)# switchport protected S5(config-if)# end S5(config-if)# S5# show interfaces g0/1 switchport
Source: CiscoPress Prevent VLAN Attacks
