The error of “User account does not have permission to open attachment” in Hyper-V Server can occur when you try to use an ISO located on a network drive as a boot drive for a VM. A workaround is to copy the ISOs on the host machine directly but that’s inconvenient and tedious. Follow these steps to fix the permissions and allow Hyper-V to use images through SMB.

User Account Does Not Have Permission
We can fix the user account that does not have permission to open an attachment in Hyper-v with two stages. The first one granting the Hyper-V server access to the network shared folder and the second stage enabling CIFS delegation on the Hyper-V machine.
To fix this issue you must have an AD domain account to grant the Hyper-V host access to the network share.
1. Grant the Hyper-V Machine Access to the Network Shared File.
- Right-click the network shared folder and open the properties then click Edit under the Security tab.
- Click Add in the new window then click on Object Types and tick the checkbox next to Computers and then press OK to apply the changes.
3. Now, type the name of the Hyper-V machine which you want to authorize on the shared folder and then press Check Names to validate. After validating the name just click the OK button to add it.
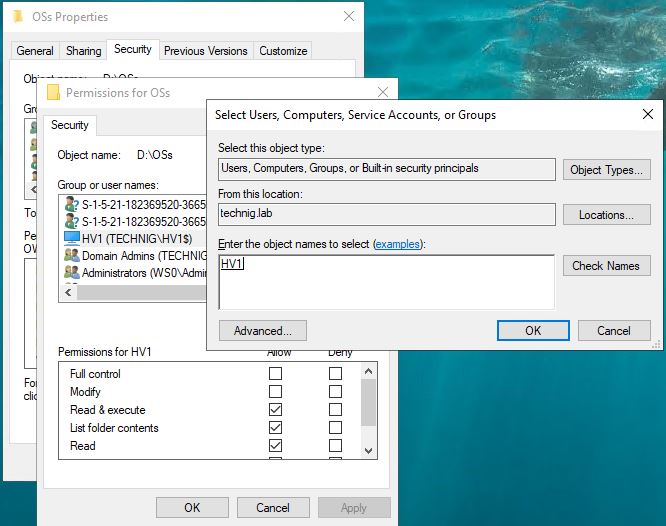
Note: If you do not tick the checkbox of Computers on Object Types the system will not find your Hyper-V machine. Make sure you’ve ticked the Computer checkbox and also your machine should be joined to the domain.
4. Click OK to close all the opened file sharing permissions windows to complete the first stage successfully.
2. Enable CIFS Delegation on the Hyper-V Machine
The CIFS delegation gives service administrators the ability to specify and enforce application trust boundaries by limiting the scope where application services can act on a user’s behalf. Service administrators can configure which front-end service accounts can delegate to their back-end services.
On your AD domain controller complete the following steps.
- Open the Server Manager then click Active Directory Users and Computers from Tools menu. Or type the dsa.msc on Windows Run to open Active Directory Users and Computers only using shortcut.
- Expand domain, and then expand the Computers folder.
- In the right pane, right-click the Hyper-V Machine name, and then click Properties.
- On the Delegation tab, select Trust this computer for delegation to specified services only and Use any authentication protocol.
- Click Add to open the Add Services dialog window.
6. Select the Users or Computers on Add Services window, and type the computer name where the network shared folder is located then validate it by clicking on Check Name and click OK.
7. Select the CIFS service for the file-sharing server and click OK to enable CIFS delegation on the Hyper-V Server.
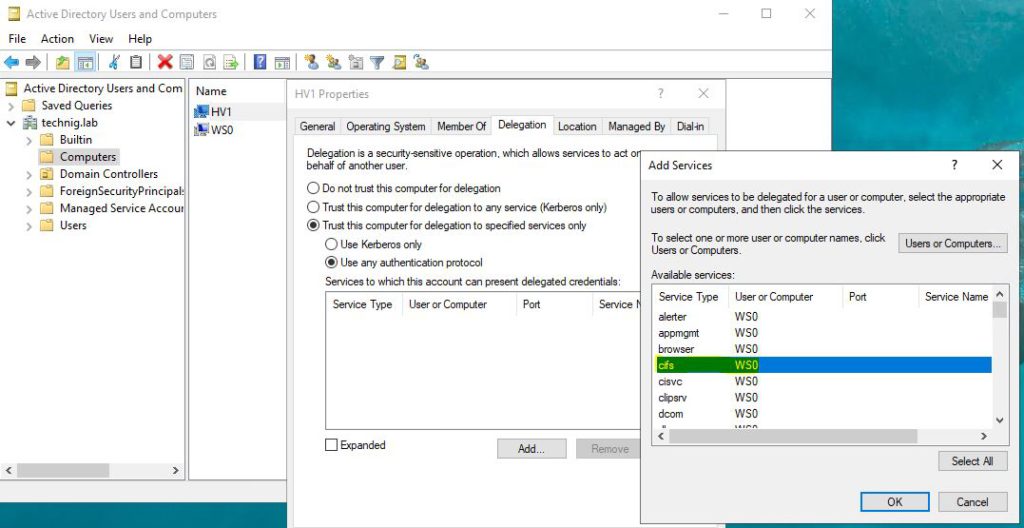
8. Finally, click OK to close all opened windows. Now you can install operating systems on your Hyper-V server virtual machines via network shared files.
Perfect, we’ve done!
